The current surge in remote working has raised cybercriminal interest in
The basic scheme is simple: Cybercriminals lure a company employee to a fake
Fake Teams messages
As a rule, when attackers send an
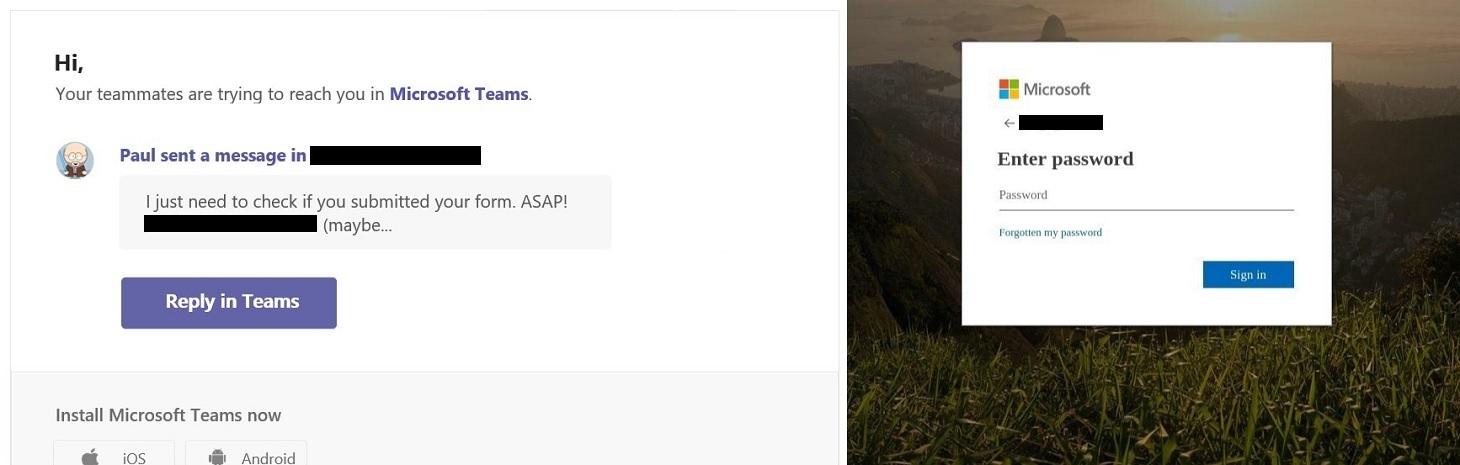
If the attackers did their homework, the name and picture of a real colleague will be in the notification, which might look something like an internal business
Delivery failure notification
Another fake problem crafted to instill a sense of urgency in the recipient is an alleged delivery failure, for example due to an authentication error. In this case, the victim was meant to click through to pick up a message, but the attackers were lazy and failed to create a plausible
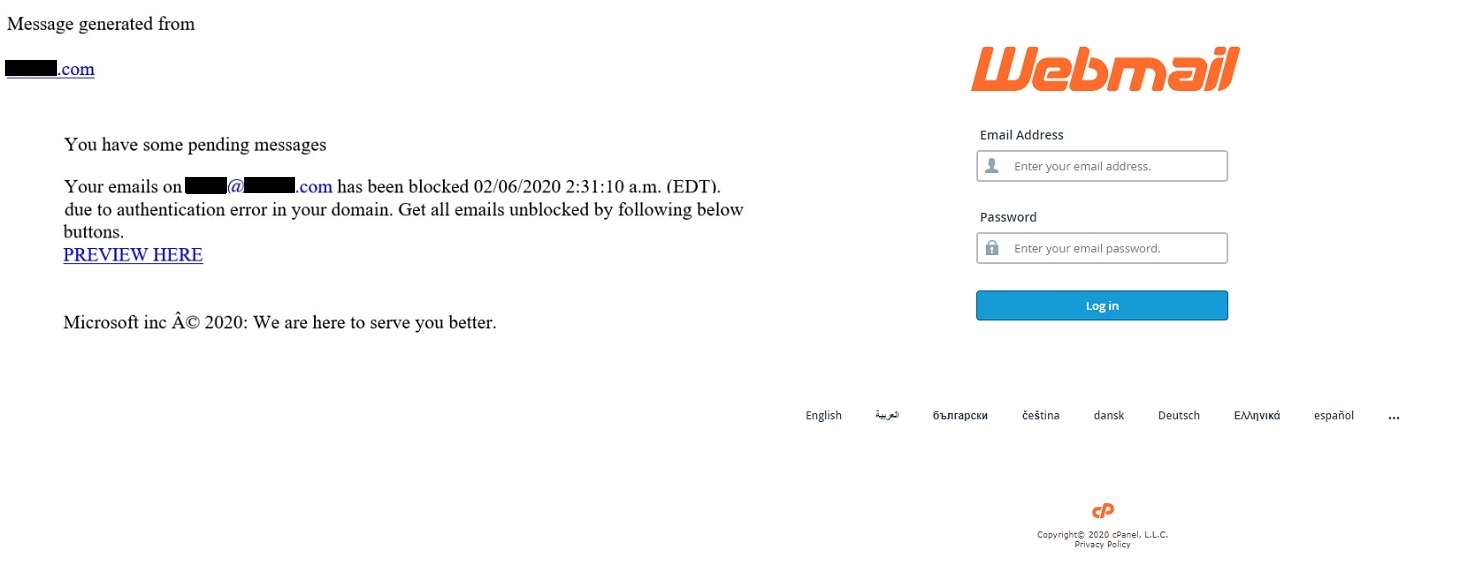
Of course, next time they might make a more convincing fake, in which case the recipient would have to fall back on other means of identifying phishing. It’s worth noting that senders, not recipients, get delivery failure notices — if the server were able to identify the intended recipient, then it would deliver the
Full mailbox notification
Warning a victim of dire consequences — in this case, the horrible prospect of an undelivered message — the full mailbox notification is simply another aspect of herding workers into a panicked error. The choice it presents is to delete or to download the messages. Most people will opt for the latter and click the bait, a “Click
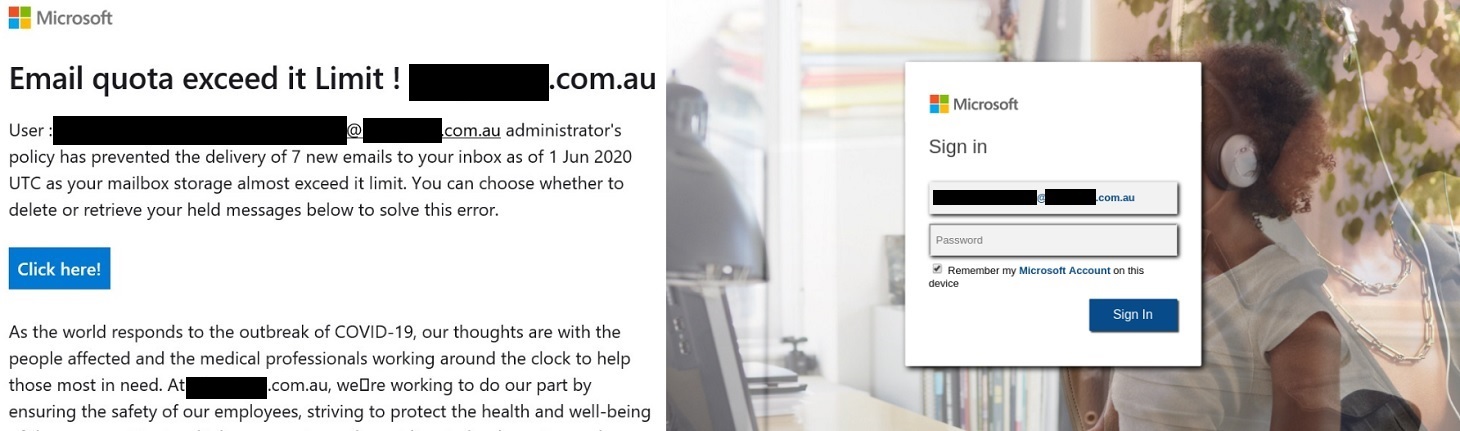
Note that in this case the attackers made some effort, inserting a paragraph in the
Password expiry notification
Changing a password is a fairly common procedure. Your company policy should require it regularly, and security may request it as a precaution against a possible leak. And, of course, when you set a new password, you have to provide the old one. Therefore,
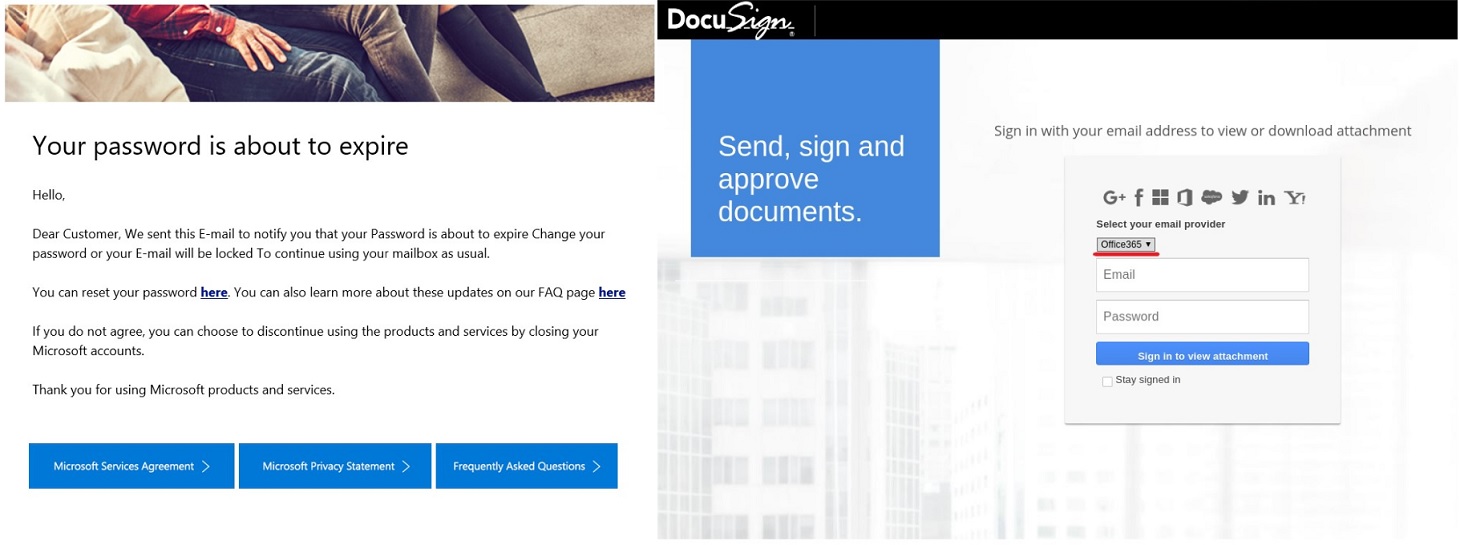
Even if you somehow miss the sloppy language in the
How to avoid getting hooked
Remember that account details unlock not only the ability to send
- Always check the address of any page asking for credentials. Depending on the service, legitimate login pages might include microsoftonline.com, outlook.office.com, onmicrosoft.com, or your company
domain name. - Deploy a robust security solution
company-wide that blocks suchphishing е-mails.
Contact Datum Consulting today to find out how we can help your business stand strong in the face of

