The COVID-19 global emergency has turned the lives of millions upside down. Social distancing and teleworking have become the norm and changed the way we communicate, work, and spend our free time. What has changed for cybercriminals? You guessed it – they have treated the healthcare crisis as
With people increasingly relying on digital tools and immersing deeper in the virtual world, hackers have ramped up their efforts to get on the hype train. From social engineering hoaxes to ransomware campaigns, the mainstream vectors of cybercrime are seeing a dramatic spike capitalizing on users’ fears and new loopholes in enterprise security precipitated by remote
Below is a lowdown on the top 5 trends in cybercrime that took root amid the
- Phishing is on the Rise
Panic is fruitful soil for scams. It comes as no surprise thatcoronavirus-themed phishing is currently gaining traction among malicious actors. These campaigns involve misleading emails disguised as alerts or advisories from the World HealthOrganization (WHO) or local healthcare institutions.
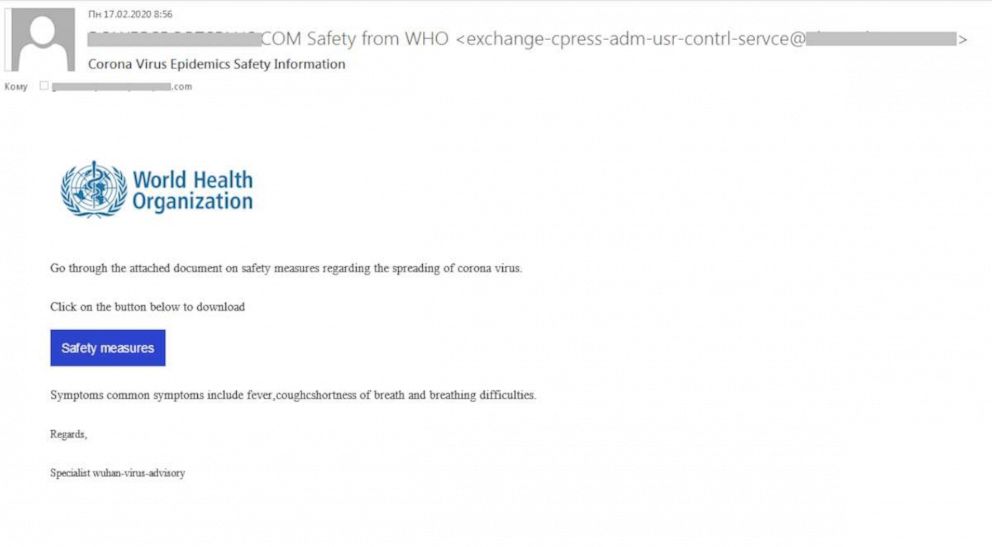 The “safety measures” email scam impersonating the WHO made its debut in early
The “safety measures” email scam impersonating the WHO made its debut in early February 2020 and became the wakeup call. It paved the way for other massive fraud campaigns of that sort. An example is a surge of the “Updated list of new cases around your city” messages pretending to come from the U.S. Centers for Disease Control andPrevention (CDC). The recipients are lured to visit a fake email verification form asking fortheir credentials.
A peculiar type of phishing called Business Email Compromise (BEC) is also gearing up for a rise. In one of these scams, perpetrators spoof corporate email to pass themselves off as representatives of a company and hoodwink customers into thinking that the organization has switched to another bank due to the coronavirus disaster. As a result, victims end up wiring funds to thewrong account. - Info-Stealing Trojans are Shifting into Hyperdrive
Info-stealers and the “infodemic” go hand in hand. This trend in cybercrime relies on a combo of social engineering and complex predatory code that harvests victims’ passwords, cryptocurrency wallets, and othersensitive details.
A particularly intricate example of this tactic is the distribution of aninfo-stealing Trojan dubbed AZORult. It arrives at computers under the guise of an interactive coronavirus map application that loadsup-to-date infection statistics from a reputable resource. However, thebooby-trapped program surreptitiously executes the stealer component as asecond-stage payload. - Ransomware Attacks Become Double Trouble
Ransomware operators who zero in organizations are increasingly adopting a tactic where data exfiltration is performed alongside malicious encryption. If a compromised company refuses to pay for the secret decryption key, crooks execute aplan B by threatening to leak the stolen files on publicly accessible resources such ashacker forums.

This trend allows criminals to negotiate with victims from a position of strength and turns these incidents into a combo of blackmail and data breaches. The cybercriminal groups behind such strains as Maze, Sodinokibi, DoppelPaymer, and Nemty have even set up special websites for thesefile dumps.
Perpetrators behind some ransomware families have recently reached out to security analysts to say that they won’t be targeting medical facilities during the coronavirus pandemic. Unfortunately, the gangs in charge of many other mainstream ransomware lineages such as Dharma and Ryuk continue to cripple IT networks of hospitals regardless. According to an INTERPOL alert issued in earlyApril 2020, ransomware attacks against critical healthcare institutions have grown significantly since theCOVID-19 outbreak. - Teleworkers Targeted on a Large Scale
The remote workforce is a new thing for numerous businesses that have been urged to implement this principle due to the coronavirus emergency. Virtual meetings are now the usual way for employees to interact withco-workers and fulfill theirday-to-day duties. The role of VPNs in this new paradigm is to keep remote workers’ connection with enterprise data assets private. The soaring use of videoconferencing software and VPN tools has encouraged black hats to look for vulnerabilities in these solutions and exploit them to stealcorporate secrets.
The bad news is, some popular virtual meetings applications turned out to be awfully insecure. For instance, the service called Zoom has security flaws that allow threat actors to infect computers with malware and snoop on users. To address the risks, companies should adopt extra privacy measures such as limiting the reuse of access codes and leveraging a dashboard to keep track ofmeeting attendees.
VPNs are also susceptible to compromise unless regularly updated and protected bymulti-factor authentication (MFA). In this context.mid-March, theU.S. Cybersecurity and Infrastructure SecurityAgency (CISA) alerted businesses to elevated risks of VPN abuse during theCOVID-19 pandemic and encouraged them to strengthen their security postures in - Pharma Spam Splashes Back onto the Scene
With users trying to stay tuned for updates about coronavirus treatment, cybercrooks have revived fake pharmacies that seem like an echo from the distant past. To promote these dubious online marketplaces, malicious actors are mainly using bots or scripts that deluge popular websites with fishy comments riddled with sketchy links. Users run the risk of clicking on these links out of curiosity, only to visit phony drug stores touting worthless or harmfulmedical products.
Summary
The latest trends in cybercrime have demonstrated that malefactors follow the headlines and don’t mind using the coronavirus theme as bait to make more victims. To avoid being scammed and falling victim to malware in these hard times, individuals and businesses should focus on enhancing their cybersecurity understanding. A few essential tips are as follows: ignore links that arrive in suspicious emails, use strong passwords, enable two-factor authentication for your sensitive accounts, and only trust updates provided by official

