We connect a lot of devices to many networks every day and sometimes we don’t realize how many networks we have connected to at the end of the day. We all use mobile devices such as cell phones, tablets and a multitude of other wireless devices. Every connection puts us at risk for things like exposing personal identifiable information, as well as encountering malware that can steal our data or otherwise compromise
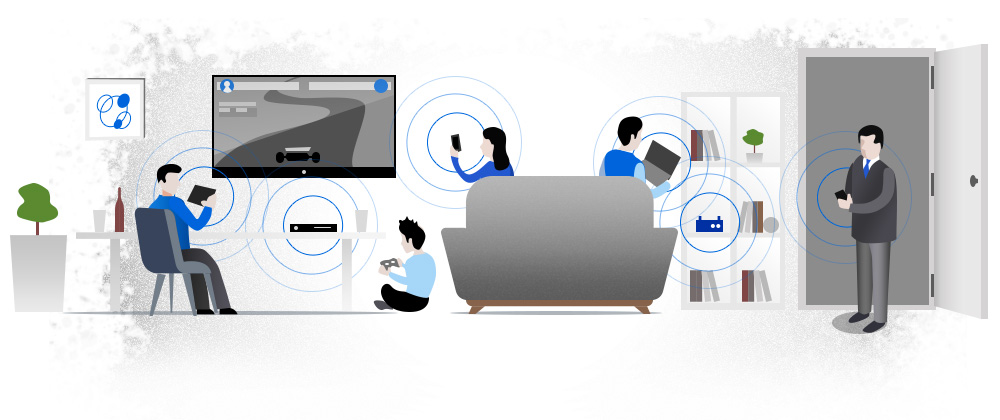
Every day we connect a myriad of devices to our home networks, the organizational network and public networks. We connect so many devices that sometimes we don’t even realize how many devices we have in our possession and we don’t even realize that some of these devices have made established connections to various internet services and they are all sharing information. We highlight the ways in which
- Rename routers and networks used at home. Don’t keep the factory default name
(i.e. Linksys). - Use strong passwords.
- Keep all your devices updated.
- Turn on encryption if available.
- Use multiple firewalls such as hardware firewalls and
software firewalls. - Turn off the WPS
(Wi-Fi protected setup) setting for yourhome router. - Use a VPN (virtual private network) when high security
is needed.
Devices such as gaming devices,
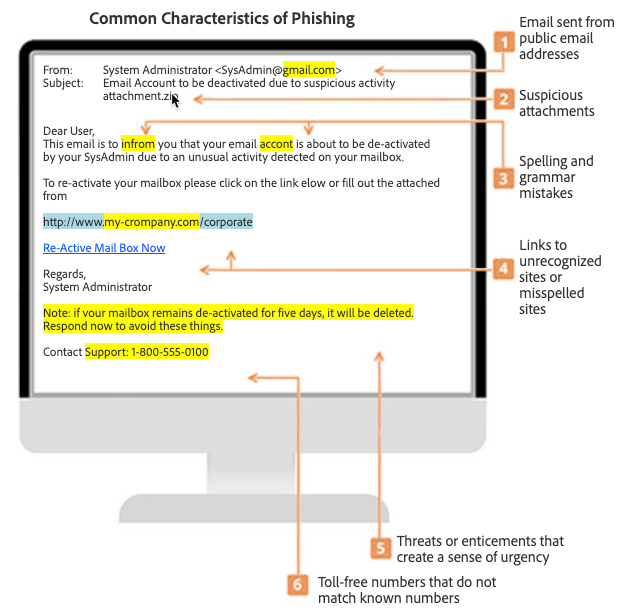
In summary, it is a tool and method attackers use to try and coerce people into clicking on a malicious site or download, potentially leading to a security issue. On the dark web, phishing is a very popular and effective way to try to steal data, lock data, delete data, gain access, or take over a computer. Phishing usually comes through email but can come via text message or other collaboration apps like Google Chat, Zoom, or other common collaboration applications. Phishing is usually obvious, and the above signs show prominently. However, some phishing attempts are tricky and it’s hard to spot a legitimate message from an illegitimate one. For example, amid the current crisis, many phishing attempts are using
Our “new normal” means that we are all working from home and learning wherever it is safe and comfortable for us. The dining table now substitutes as our mobile office and a hammock tied to a tree in the backyard could also substitute as a conference room. This freedom is great for our “new normal” but we must be cognizant that everything we do online has potential risks that can compromise your data. It is important to always be conscious of what content you’re accessing online, where you’re accessing it and what device you’re using to access that content. Because of this, if you connect it,

